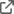User sessions are managed via your IDP. Access token lifetime can vary from 60 to 90 minutes.
So once the session expires, the user would normally have to sign-in again.
How to overcome this?
With the OIDC workflow, it is possible to retrieve a new access token without prompting the user to provide credentials again. This is done by finding a valid access token from cache or by finding a valid refresh token from cache and then automatically use it to redeem a new access token.
The diagram below shows the normal OIDC workflow:

Below you can find a sample code snippet which uses the acquire_token_silent method available through the class: msal.PublicClientApplication:
def authenticate_azure(app):
accounts = app.get_accounts()
if accounts:
print("Taking the token silently")
creds = app.acquire_token_silent(SCOPES, account=accounts[0])
else:
print("Taking token interactively")
creds = app.acquire_token_interactive(scopes=SCOPES, port=PORT)
return credsYou can find the full code sample below, which uses both the acquire_token_interactive and acquire_token_silent methods:
import atexit
import os
import asyncio
from cognite.client import CogniteClient,ClientConfig
from cognite.client.credentials import Token
from msal import PublicClientApplication, SerializableTokenCache
from cognite.client.data_classes import ExtractionPipeline
TENANT_ID = "<tenant_id>"
CLIENT_ID = "<client_id>"
CDF_CLUSTER = "<cluster>" // Ex: api, westeurope-1 etc
COGNITE_PROJECT = "<Your_Project>"
CACHE_FILENAME = "cache.bin"
BASE_URL = f"https://{CDF_CLUSTER}.cognitedata.com"
SCOPES = [f"https://{CDF_CLUSTER}.cognitedata.com/.default"]
AUTHORITY_HOST_URI = "https://login.microsoftonline.com"
AUTHORITY_URI = AUTHORITY_HOST_URI + "/" + TENANT_ID
PORT = 3000
app = PublicClientApplication(client_id=CLIENT_ID, authority=AUTHORITY_URI)
def create_cache():
cache = SerializableTokenCache()
if os.path.exists(CACHE_FILENAME):
cache.deserialize(open(CACHE_FILENAME, "r").read())
atexit.register(lambda:
open(CACHE_FILENAME, "w").write(cache.serialize()) if cache.has_state_changed else None
)
return cache
def authenticate_azure(app):
accounts = app.get_accounts()
if accounts:
print("Taking the token silently")
creds = app.acquire_token_silent(SCOPES, account=accounts[0])
else:
print("Taking token interactively")
creds = app.acquire_token_interactive(scopes=SCOPES, port=PORT)
return creds
app = PublicClientApplication(client_id=CLIENT_ID, authority=AUTHORITY_URI, token_cache=create_cache())
def get_token():
return authenticate_azure(app)["access_token"]
cnf = ClientConfig(client_name="my-special-client", project=COGNITE_PROJECT, credentials=Token(get_token), base_url=BASE_URL)
client = CogniteClient(cnf)
print(client.iam.token.inspect())


 Check the
documentation
Check the
documentation Ask the
Community
Ask the
Community Take a look
at
Academy
Take a look
at
Academy Cognite
Status
Page
Cognite
Status
Page Contact
Cognite Support
Contact
Cognite Support