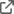Request you to share on how to add environment specific URL(dev/prod/test) in handler.py in AIR. Also need to understand on how to get msal_token (bearer) authorization in AIR functions.
Example:
msal_token = request.headers.get("authorization")
requests.get(sequence_generator_api, headers={"authorization": msal_token})
where sequence_generator_api is environment specific API


 Check the
documentation
Check the
documentation Ask the
Community
Ask the
Community Take a look
at
Academy
Take a look
at
Academy Cognite
Status
Page
Cognite
Status
Page Contact
Cognite Support
Contact
Cognite Support