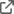We are trying to connect CDF Project instance : accenture-demo-dev through python SDK. We are getting the below error :
Cognite API error : Resource not found. This may also be due to insufficient access rights. | code: 403 | X-Request-ID: 941c405e-bd77-9105-9485-4bfe9575c998
We have provided all capabilities access to this project.
cdf project link : https://accenture.fusion.cognite.com/accenture-demo-dev?cluster=api.cognitedata.com

Best answer by ShylashriSelvamani
View original

 Check the
documentation
Check the
documentation Ask the
Community
Ask the
Community Take a look
at
Academy
Take a look
at
Academy Cognite
Status
Page
Cognite
Status
Page Contact
Cognite Support
Contact
Cognite Support